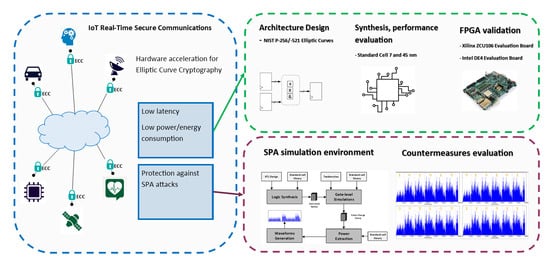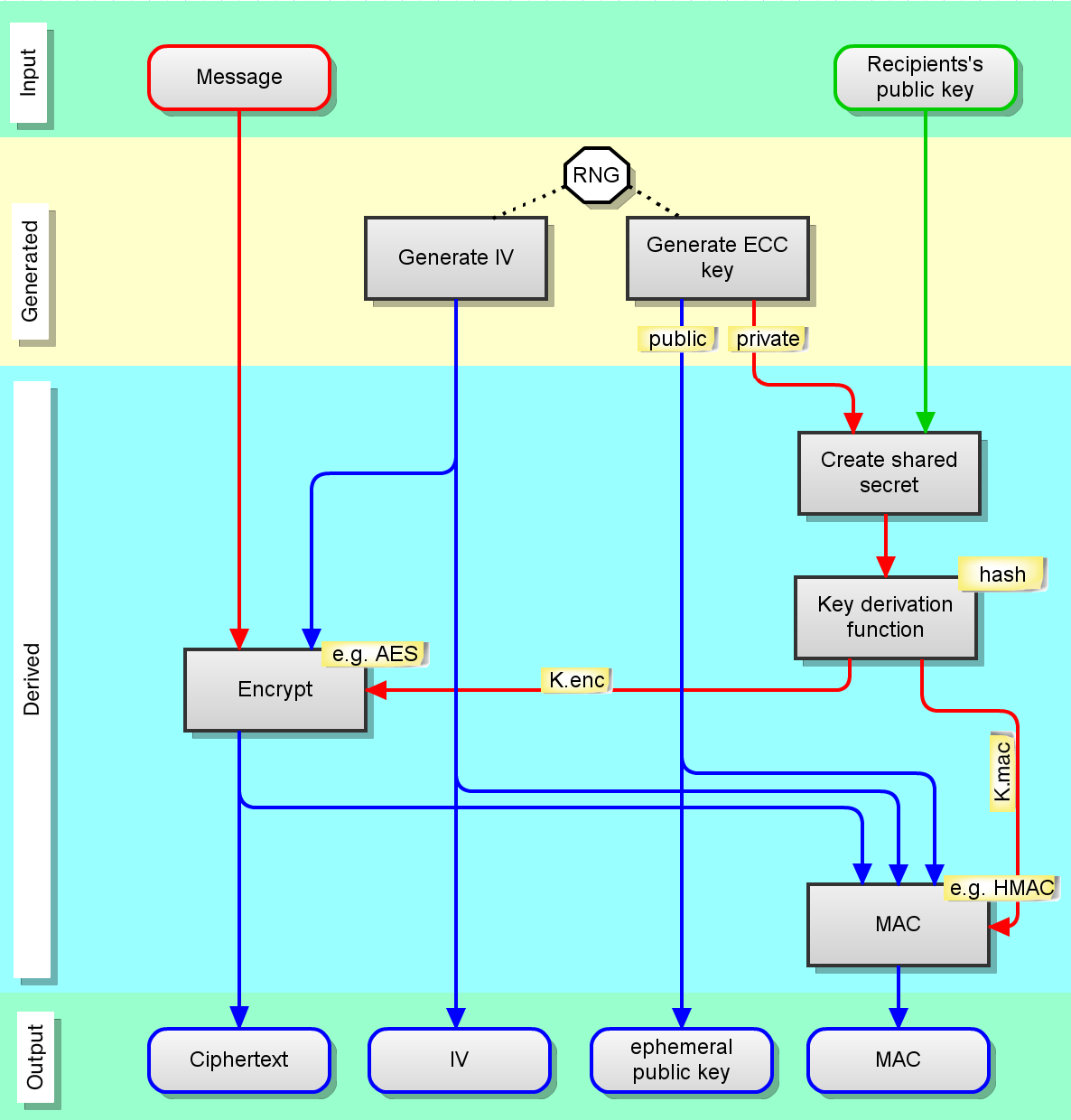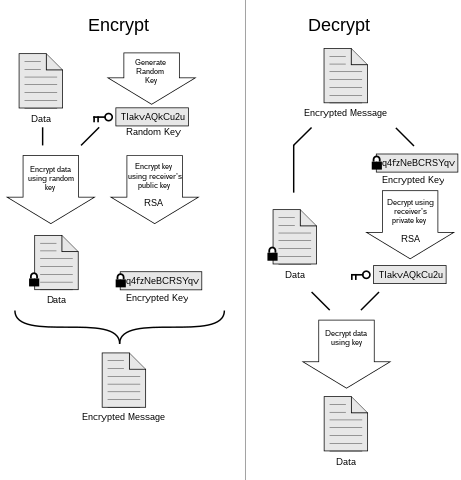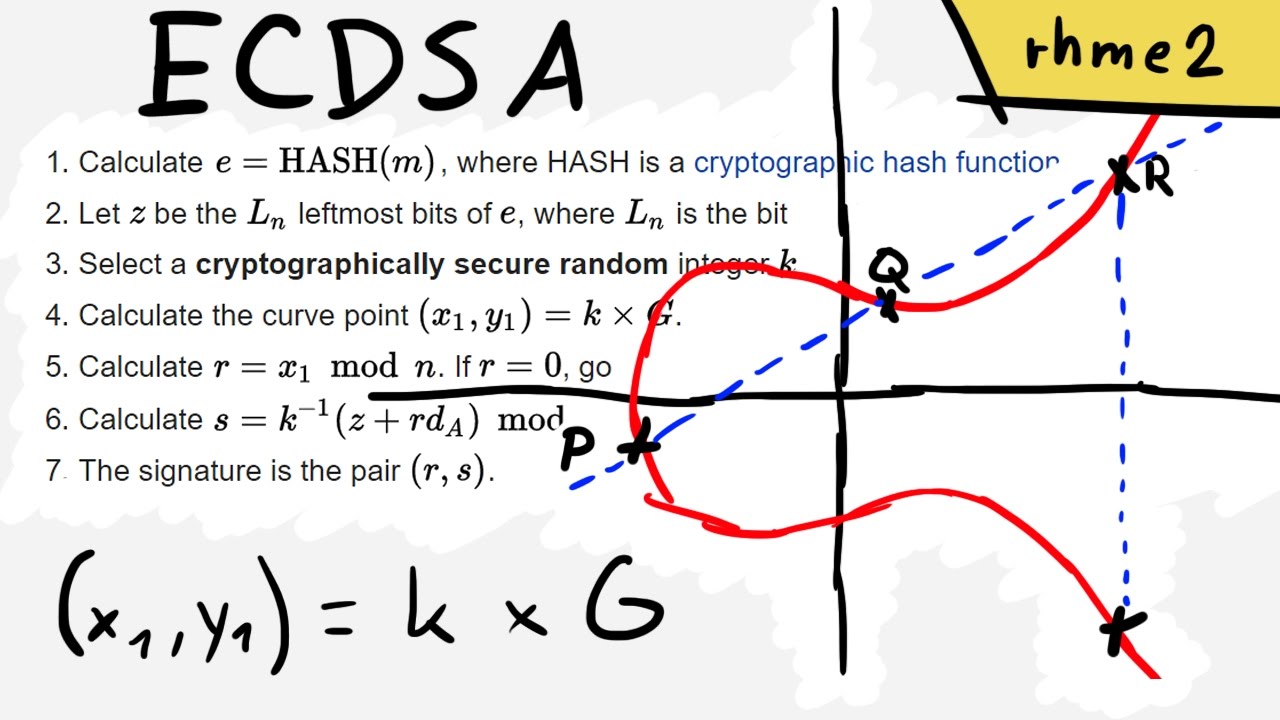
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150) - YouTube
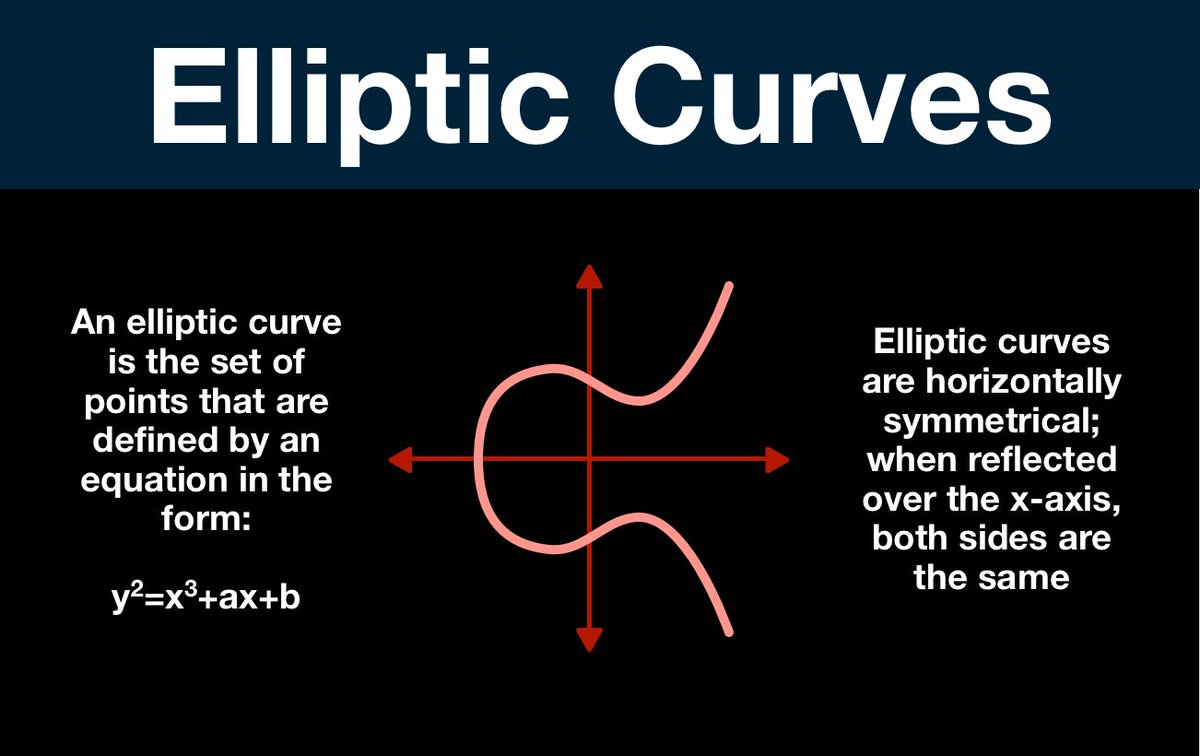
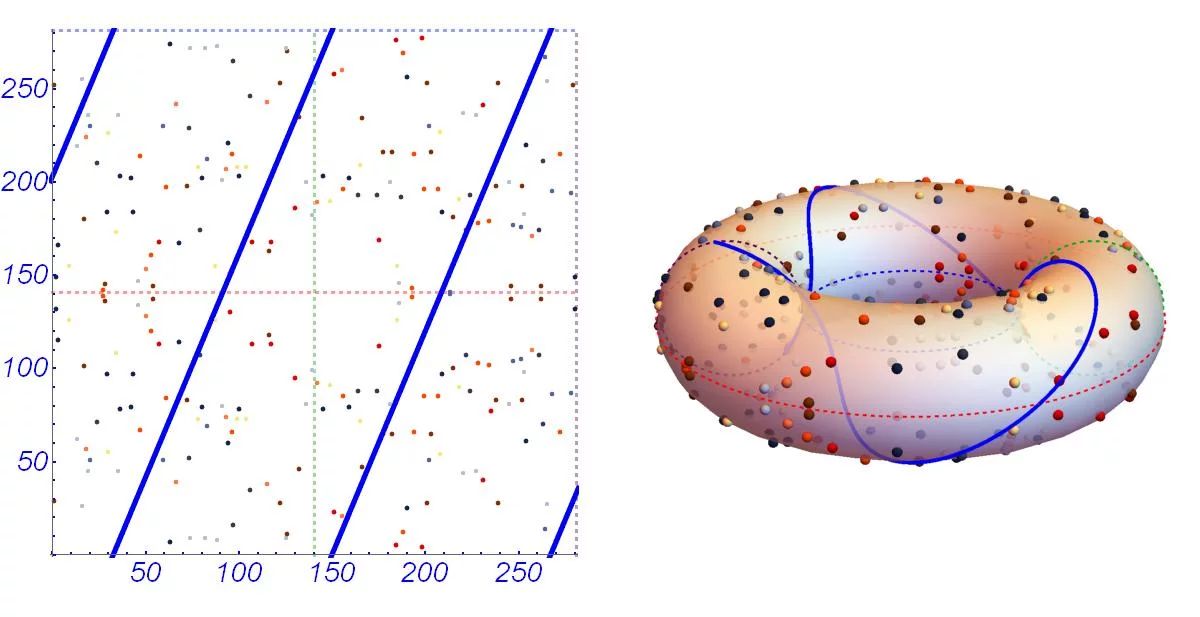
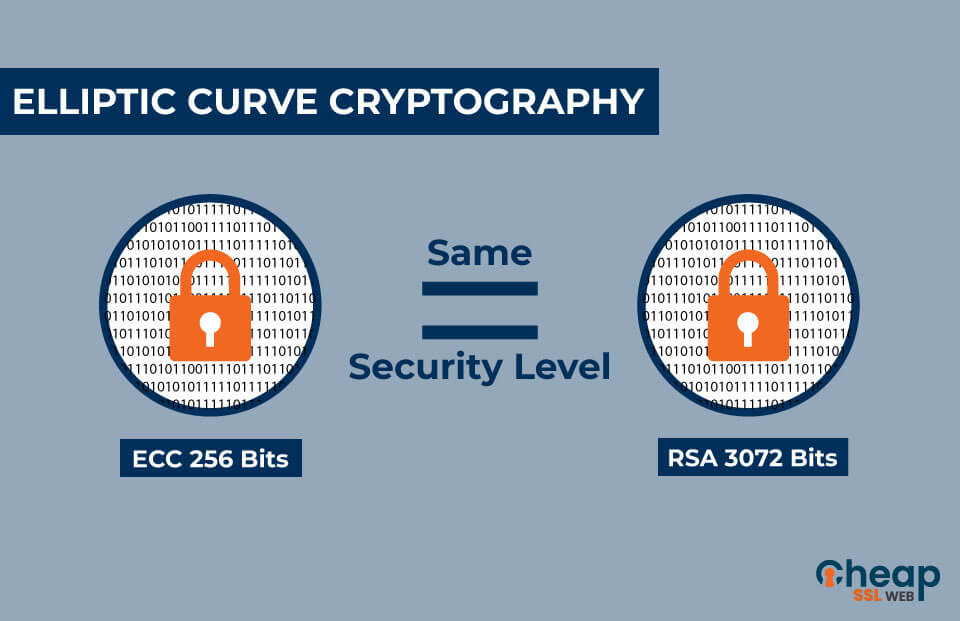
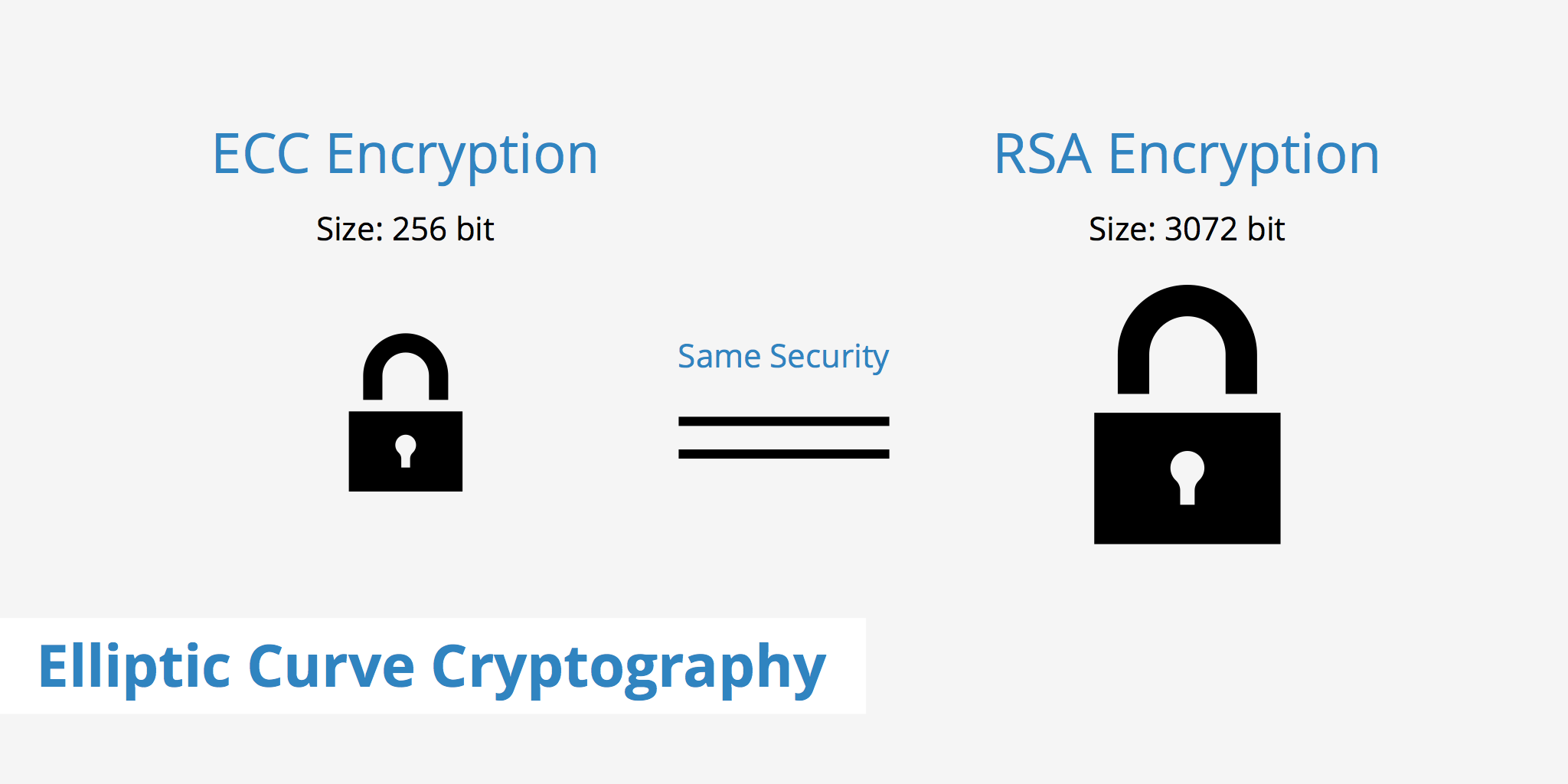
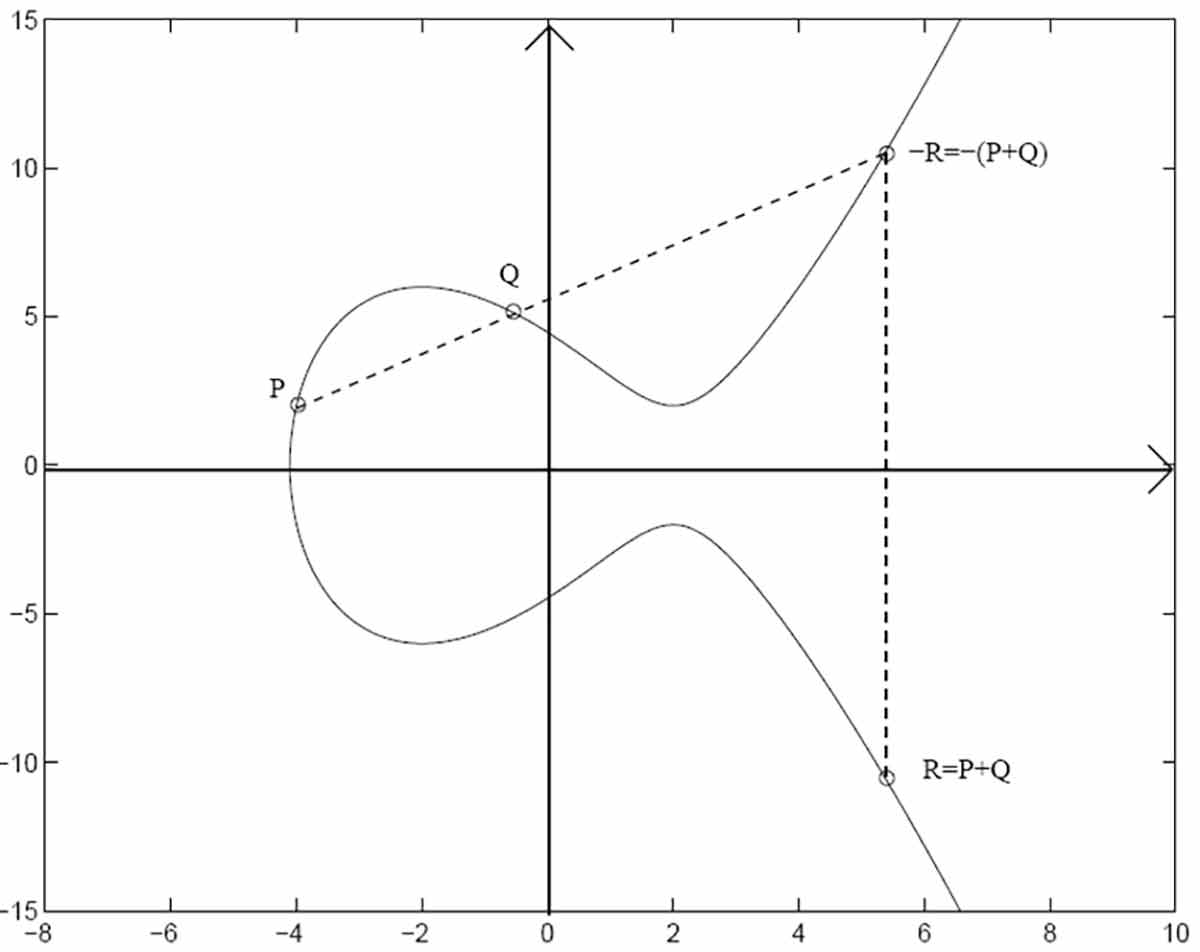
Tyrannosaurus Haym on Twitter: "(1/25) Cryptography Fundamentals: Elliptic Curve Cryptography Elliptic Curve Cryptography is (one of) our strongest cryptographic tools, vastly more secure than its predecessors. But... how does the moon math